Vulnhub — Drifting Blues 3 Write-up

Difficulty: Easy
Resources: -
Link to the machine on Vulnhub
Video Solution by Proxy Programmer
Nmap Scan

Cool, port 80 (http) and 22 (ssh) is opened. We’ll return for the disallowed entry (/eventadmins) on robots.txt later on.
_________________________________________________________________
Gobuster Results

Went over each of the discovered directories, they are full of repeating sequence of alphabets (ABABAB…/ABCABCABC…). So, not much useful information there.
_________________________________________________________________

Back to the disallowed entry (/eventadmins) on robots.txt. Here, we are instructed to visit /littlequeenofspades.html.
_________________________________________________________________

At the bottom seems to be a base-64 encoded string, let’s decode it.
aW50…PQ== → intruder? L2FkbWluc2ZpeGl0LnBocA==
L2Fk…cA== → /adminsfixit.php
(FYI, CyberChef is a handy tool for such things if you’re just starting out)
_________________________________________________________________

On /adminsfixit.php, the author has given us a hint of “ssh auth log”, which means ssh poisoning should be possible.
_________________________________________________________________

Here, we are making use of the username in ssh to inject a piece of PHP code, which would run commands supplied to the “payload” variable later on.
_________________________________________________________________

Back to /adminsfixit.php, the PHP code we have injected earlier would execute commands supplied to the “payload” variable through the usual GET request.
Now that we’ve confirmed Netcat is available on the target system, let’s try to get ourselves a reverse shell.
_________________________________________________________________

Setting up Netcat listener on port 8888
_________________________________________________________________

Initiating a reverse shell.
_________________________________________________________________

Obtained a reverse shell.
_________________________________________________________________

Under the home directory of user “robertj”, there’s an /.ssh folder which we (www-data) have the permission to write into.
For those unfamiliar, this is sign of possible horizontal privilege escalation. Once we’ve inserted our public key into authorized_keys of robertj, we’ll be able to ssh our way in as robertj without needing of a password.
_________________________________________________________________

Generating RSA key pair.
_________________________________________________________________

Extracting our public key.
_________________________________________________________________

Now, let’s write our public key into authorized_keys of robertj.
Also, make sure robertj has read permission on the authorized_keys created by us (www-data).
_________________________________________________________________

SSH-ing our way in.
_________________________________________________________________

Flag 1 of 2
Privilege Escalation
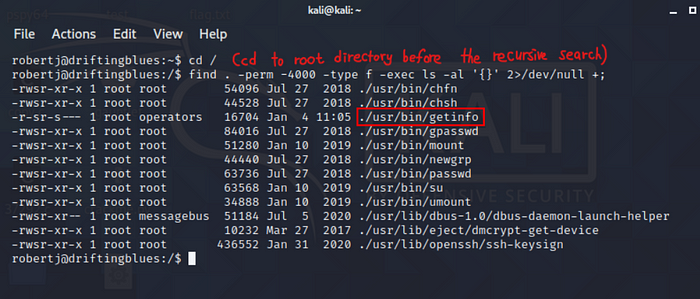
Searching for setuid bits enabled files. One particular file, ./usr/bin/getinfo seems interesting.
_________________________________________________________________

Running the getinfo executable.
The executable seems to be consist of three commands:
ip a
cat /etc/hosts
uname -a
Assuming that these commands aren’t called by their absolute path (e.g. /usr/bin/ip, /usr/bin/uname), we might be able to leverage environment variables in such a way that our malicious version of ip / uname would be executed, instead of the ones in /usr/bin.
_________________________________________________________________

Creating our version of uname, which consists of a bash shell.
Chmod 777 so that it can be executed by other users.
_________________________________________________________________

Adding /tmp to the front of $PATH variable, so that our version of uname will be found first and executed, instead of the one in /usr/bin.
_________________________________________________________________

Moment of truth! Let’s try running /usr/bin/getinfo
And there we have it! A root shell!
_________________________________________________________________

Flag 2 of 2 !
Overall, an enjoyable box. Great learning opportunity for beginners (like myself!).